Logging into Verizon.com
I log into Verizon’s Small Business portal once a month to pay my bills. Generally speaking, their site is atrocious. It’s clearly the product of committee thinking and their fractured corporate structure.
They recently implemented a redesign of the login portion, and somehow they resurrected good ol’ Frank Kafka and put him on the committee.
I may have buried the lede of this story. So unless you just enjoy reading my rants, skip right to it.
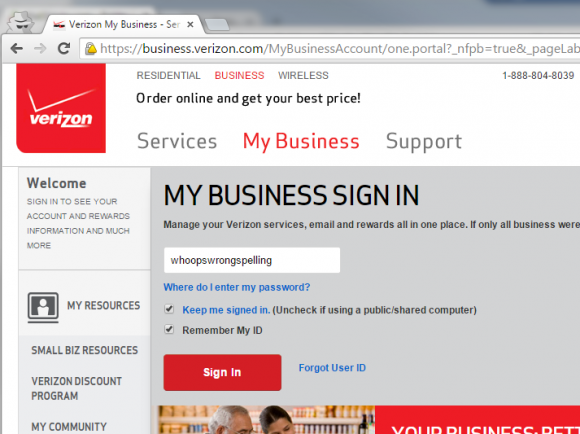
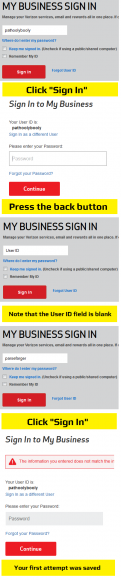
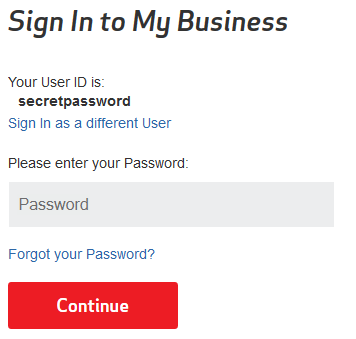
The initial login screen
As with many banking and commerce websites, Verizon has implemented a separate page for your username which precedes the password entry page. This is good security practice and so I have no problem with it in general.
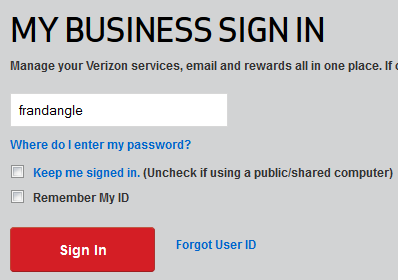
Just for the example here, I’m using the username whoopswrongspelling. What really happened was that I transposed two characters in my username, so it might as well have been whoopswrongspelling. That was my mistake, of course, but it’s a mistake that’s sufficiently common that it shouldn’t cause the website to malfunction.
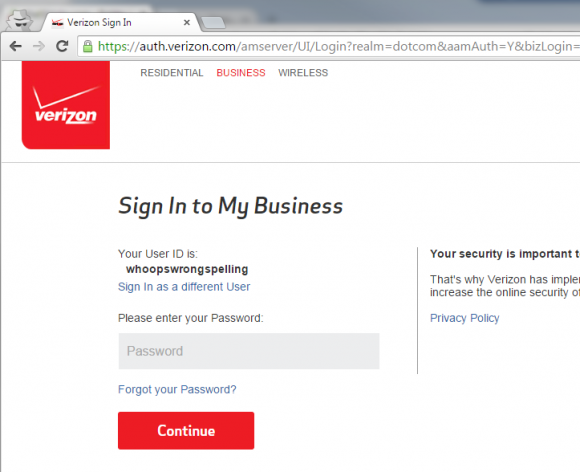
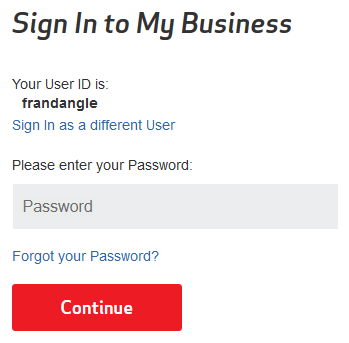
And so I’m prompted for my password. Perfectly normal so far. I’d realized that I had misspelled my username, so I did what a normal user would do and hit the back button.
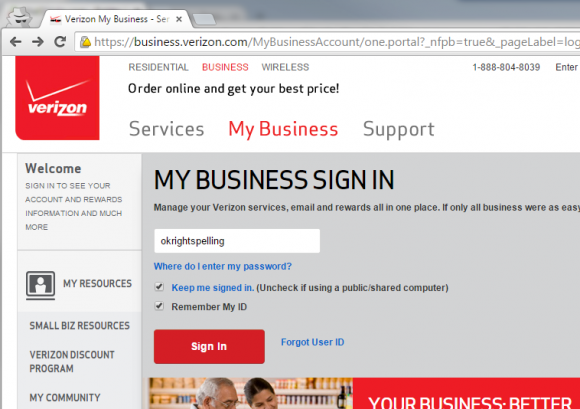
I correctly entered my username (again, I’m obviously just using okrightspelling as an example here, though maybe that’s what Tori Spelling uses as her login).
No, that’s not a re-post of the first screenshot.
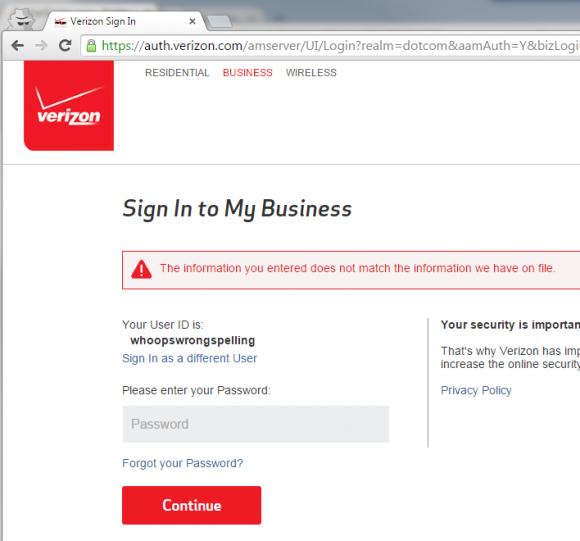
Even though the first username I’d entered was completely invalid they chose to store that information and ignore the correct username I’d since entered.
The Solution (is Obvious)
Of course, it’s not a completely circular corkscrew of illogic. There is quite obviously a “Sign in as a different User (sic)” link on the password entry page. However, I was never signed in as the user whoopswrongspelling and I can only assume that such a user doesn’t exist.
Despite there being an obvious solution, there are still two separate bugs causing this problem:
They shouldn’t be saving an invalid username in the session (or via cookie and database — whatever). That just doesn’t make sense.
Also, a subsequent login attempt should overwrite the prior login attempt. Once I’d entered okrightspelling and hit “Sign in”, that should have obviated the existing login. That’s both for reasons of privacy and security as well as practicality.
If Only I Could Tell Verizon…
I’m going to post a link to this rant on Verizon’s Facebook page. But otherwise there’s no official channel by which I can report website bugs.
There’s a section on their website to report security vulnerabilities but the issue at hand more represents a frustration and a lack of best practices than a security vulnerability. Actually, this is a security vulnerability.
If you want to talk to Verizon, their customer service infrastructure is where Josef K would feel right at home. Do you have an issue with a POTS line and your FiOS TV? Oh, that’s two different departments, so I’m going to have to transfer you. Or, you’re a business customer, huh? Well, you’ll have to call the business center back between the hours of 9-5 Monday through Friday.
The Security Vulnerability
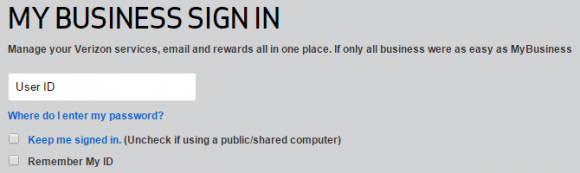
When logging in on my home computer, I’d checked the box to “Remember My ID“. I assumed that was why my username was being saved, but it turns out that I was wrong.
I just opened a clean private browsing session and did the same test. The results were the same.
That kinda ruins the whole point of improving security via a two-step login process.
This indicates to me that if you were to attempt to login to Verizon’s site on a public or shared computer, the next user would be able to see your username, even if you did not opt to have it saved.
Of course, this only is a problem if you fail to login. But this would effect anyone that forgets their password and for whatever reason doesn’t complete the “forgot password” process. That seems like a rather improbable case, but consider that Verizon has tens (hundreds?) of thousands of small business customers, so even if that only effected 0.1% of users it would effect a lot of people.
Make that: “Millions of Customers”
Their residential customers uses the same login forms. So if they have 10 million customers that can login to their internet portal (which is not an improbable number) and this bug effects only 0.01% of them, that’s still ten thousand customers.
Test it for Yourself
Make up a couple of really improbable usernames, and go to the login page.
But Wait! There’s More!
This is the security bug to end all security bugs (that I’ve found so far).
Try this:
Step 1: Open a fresh, clean, private browsing session and go to Verizon’s small business login page.
Step 2: Enter a username and click the “Sign In” button. I found this bug using my real username, but it also works with a fake one, so enter whatever you want.
Step 3: Wait 10 minutes. That’s right, have some patience and just let your browser sit on this page for about ten minutes. I don’t know that 10 minutes is a magic number, just that I personally don’t have the patience to try decrementing time intervals to find the floor of the time frame.
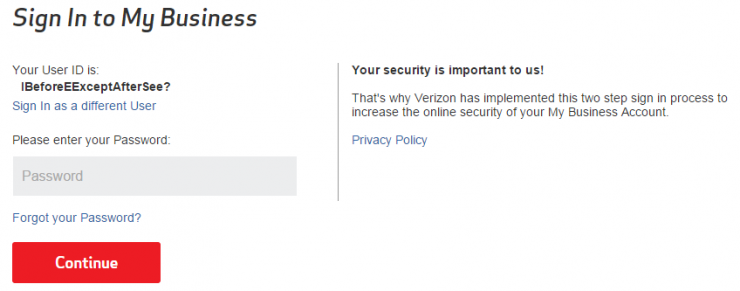
Step 4: Now that it’s been 10 minutes, enter your password in the “password” box. Use a fake password, though. Again, when I first found this bug I was using my real user ID and my real password, but a fake one works just the same and is recommended for reasons that will become obvious.
Step 5: Observe that your password is displayed in plain text under the words “Your User ID is”.
I swear that I’m not making it up. These are actual screenshots that I took while going through those exact steps.
Oh man, that’s a doosie.
I can only imagine that Verizon’s servers have some sort of timeout after which they confuse the password field with the username field. But how in the holy heck did the developers even manage that? And how little testing and code review did they do before pushing this code out for use by their millions of customers?
Again, this won’t effect everyone, but I fell upon it by accident when I got a phone call in the middle of the two-step login process. If I was trying to login at say, an airport or a coffee shop (I hear that’s where normal people go to web browse), anyone looking over my shoulder would have seen my password.
But wait! There’s EVEN MORE!
Since I originally posted this rant, this Verizon thing has been nagging at the back of my mind. One burning question, actually: What else is there?
There’s no way that they could have made both a buggy and sloppy login process as well as one that’s secure and trustworthy. I’m no "hacker", so I don’t want to delve too deep into this and risk any kind of legal action, however…
That’s what they call SQL injection. You put a piece of SQL in a website’s input box, with the hope (or in this case worry) that it will be executed.
I should note that the SQL query I injected was not destructive and would not reveal customer data to me. I’m not trying to compromise Verizon’s database maliciously, but rather trying to see if it could be compromised.
That doesn’t look like a big deal, right? No secret data was revealed, and there was no catastrophic failure.
Well, as a developer that has written many a login form, let me tell you that it is a big fracking deal.
The word “null” should never be shown to the end user in this sort of context. Never. When a null is spit out by a database or some user interface code and makes it to the user’s screen, that means that something completely unplanned went wrong.
What should have resulted was a nice, polite error on the second login page along the lines of “I’m sorry, but there was an error with your login attempt. Please try again”. Period. End of discussion.
And SQL injection attacks are extremely common. So it’s something for which every web developer (let alone the development team at a multi-billion dollar company) should forsee and for which they should plan.
While this simple emission of “null” from the website is superficially minor, it tells a story: That they didn’t do even basic testing on this login process. It also may mean that my SQL injection did work, but the results of my injected query didn’t percolate up to the user interface.
But something like a DELETE statement doesn’t need to return a result set.
Next, I figured I’d take a peek at the HTTPS traffic going back and forth with Verizon. There was nothing earth shattering, but there is this:
It is bad practice to put the type, let alone version, of your webserver in your response. Why? A few reasons, but chiefly because it tells potential attackers exactly which vulnerabilities to try exploiting first.
Certain versions of certain web and application servers have particular vulnerabilities. Knowing which one they’re targeting is a huge leg up for a malicious “hacker”.
Moreover, because I now know that they’re using Oracle iPlanet and Oracle OpenSSO, I can be reasonably certain that their data is stored in an Oracle database. It only makes sense, right? So now a black hat would also have a solid starting point for any kind of SQL-centric attack.
Do you trust these guys with your personal information yet?
Another crazy thing is that the login form seems to allow for unlimited characters in the user ID field, and there is no pre-processing to truncate the field. It will POST the entire string.
Interestingly, if I threw a ~1,000,000 character string of zeros into the field I was immediately 302 redirected to another login page. (The browser truncated my input to ~27,000 characters during the form submission.)
Again, that should result in a user-friendly error, not a mysterious redirect.
By the Way, Verizon
At least keep your capitalization and punctuation consistent. I don’t grammar-police people on the street, because rules are meant to be broken in casual conversation and in rants on s.co.tt. But you are a multi-billion dollar company writing a very formal website. Details should matter to you.
If it were one tiny mistake out of pages of text, of course I’d forgive you. But in these two simple portions of what should be two simple web pages, you frucked up quite a lot.
- In all the other places that I’ve seen it mentioned, your portal’s branding is “My Business”. Yet you’ve omitted the space between those two words in the sentence “If only all business were as easy as MyBusiness”.
- Speaking of that same sentence, there is no period at the end of it.
- One more thing about that sentence: You’ve consistently used the word “business” in the context of “my [small] business”, meaning a company; A singular noun. Yet here you’re using it first in the plural sense of activities of a business-like nature, then in the sense of “MyBusiness”, the implied form of a singular noun. The point is that it seems out of place here and reads poorly due to too much cleverness and too little utility.
- The phrase “Keep me signed in” ends in a period, but neither “Uncheck if using a public/shared computer” nor “Remember My ID” ends in one.
- To again contrast two of those phrases: The word “My” is capitalized as if part of a title, but the preceding option label did not capitalize “me” nor “signed” in a similar style. It’s just an odd discrepancy seeing as they’re contextually identical.
- The text of the “Forgot User ID” link capitalizes the word “user”. User is neither a proper noun, nor is that phrase part of a title. (I realize that you may be referring to some kind of perceived elevation of the User such that it’s become a proper title, however that doesn’t jibe well with me.)
Sorry to go on, but I have a few simple design points as well:
- Why is “Where do I enter my password” a link? It just opens a tiny popup with two short sentences of explanation. Why not just put the explanation on the page, and not make the user work for it?
- The “Forgot User ID” link is not aligned with the “Sign In” button. It looks like it’s lost in space.
- This is more of a preference than a rule, but generally (which is to say on every other website) temporary field values are in grey or another non-input-entry color. In other words, in the “User ID” text box, the phrase “User ID” should be a lighter or different color to the text of the user ID entered by the actual user.
As for this page:
- I can’t help but notice that the login on the previous page was entitled “MY BUSINESS SIGN IN”, yet here the title is “Sign In to My Business”. It’s just inconsistent is all. I’d be accepting of either, but not both.
- The word “in” should not be capitalized in the title of this page.
- Again, you seem to be suffering under the misconception that I am the Official and Only User and that I have a User ID.
- I see that Password has also been elevated to the position of an Official Title. I feel so important! (This occurs twice on the page).
- There’s a sentence on the right side of the page that bothers me. It ends in the words “your My Business”. I’ll grant that it’s clear and correct that “My Business Account” is the title of this area. (Or is it? Until now you’ve never added the word “account” after the title “My Business”.) Anyway, my point is that “your my” sounds bizarre. A better turn of phrase might have been simply “[..] online security of your account”.
- “Sign In as a different user”. Again, your Capitalization Addiction rears its Ugly Head. (I’m still trying to get over my hyphen-addiction, so I feel for you.)
I only have one design note for this particular area:
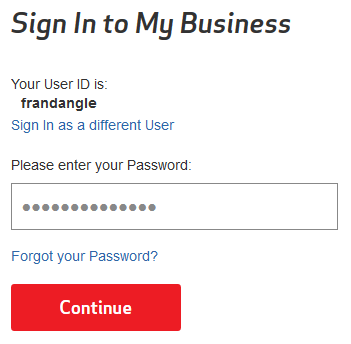
- Whereas on the previous page I complained that the default text in the “User ID” box was the same black as a user’s entry, in this page you’ve completely switched styles to a border-less grey box containing a darker grey default text for the “Password” input.
I know that I’m nitpicking. I like to nitpick. But it makes the point that even with giant committees, billions of dollars, and a labyrinthine corporate structure you can still miss the details. It also sends a bad message.
Haphazard and slapped together is not what I want to picture when thinking of my telecommunications carrier.
Update: 2015-04-22
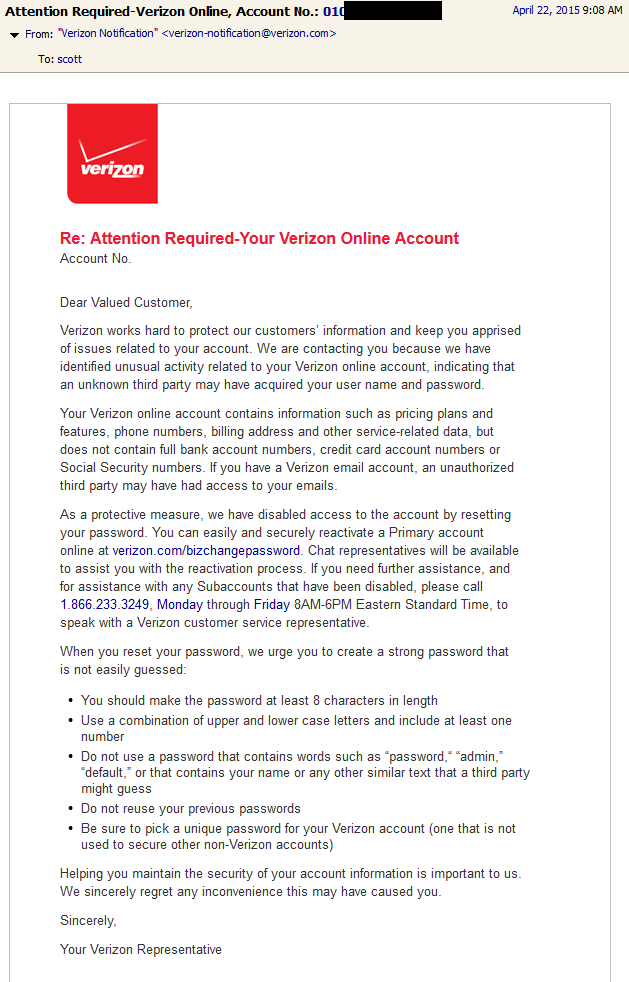
It’s been about a week since I posted the above rant. Today I received an email from Verizon stating that my account may have been compromised and that my password has been changed.
Of course my first thought was that this was a phishing email (I don’t know my own VZ account number offhand to confirm). And by the way before you click on a link in any email, check the bottom of your web browser window to confirm the destination. I did that, and they were in fact linking me to verizon.com.
While it’s completely possible that my account was coincidentally compromised within a week of my rant, I like to think that it just took them a week to catch up with all my crazy login attempts that I made while testing out their login process. Is that the case? I’ll probably never know.
It Keeps Getting Worse
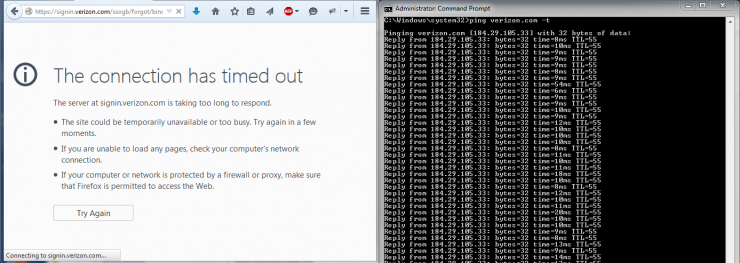
In that email they advise that I can easily and securely reactivate a Primary account online at verizon.com/bizchangepassword. Great! Let’s do that.
The link that they provided in the email redirects to signin.verizon.com. As you can see from the screenshot, that site is down. And just so you don’t think that my internet connection is faulty, I opened up a ping to verizon.com. Unfortunately signin.verizon.com wasn’t responding to a ping, though it did resolve in DNS.
That’s very disheartening. My ISP’s site is down. Meanwhile, my personal rambles on this blog are perfectly accessible. Guy with servers in his basement: 1, multi-billion dollar national corporation: 0.